Anycast Geo-DNS determines how quickly, securely, and reliably users can access your content today. I will show you the technical differences, real-world applications, and a clear decision-making process that will help you choose the right smart DNS routing strategy in 2025.
Key points
- Anycast: Automatic proximity, very low latency
- Geo-DNSTargeted control, regional rules
- DDoSDistribution protects global name servers
- ComplianceData locations and language versions
- Hybrid: Automatic plus rules combined

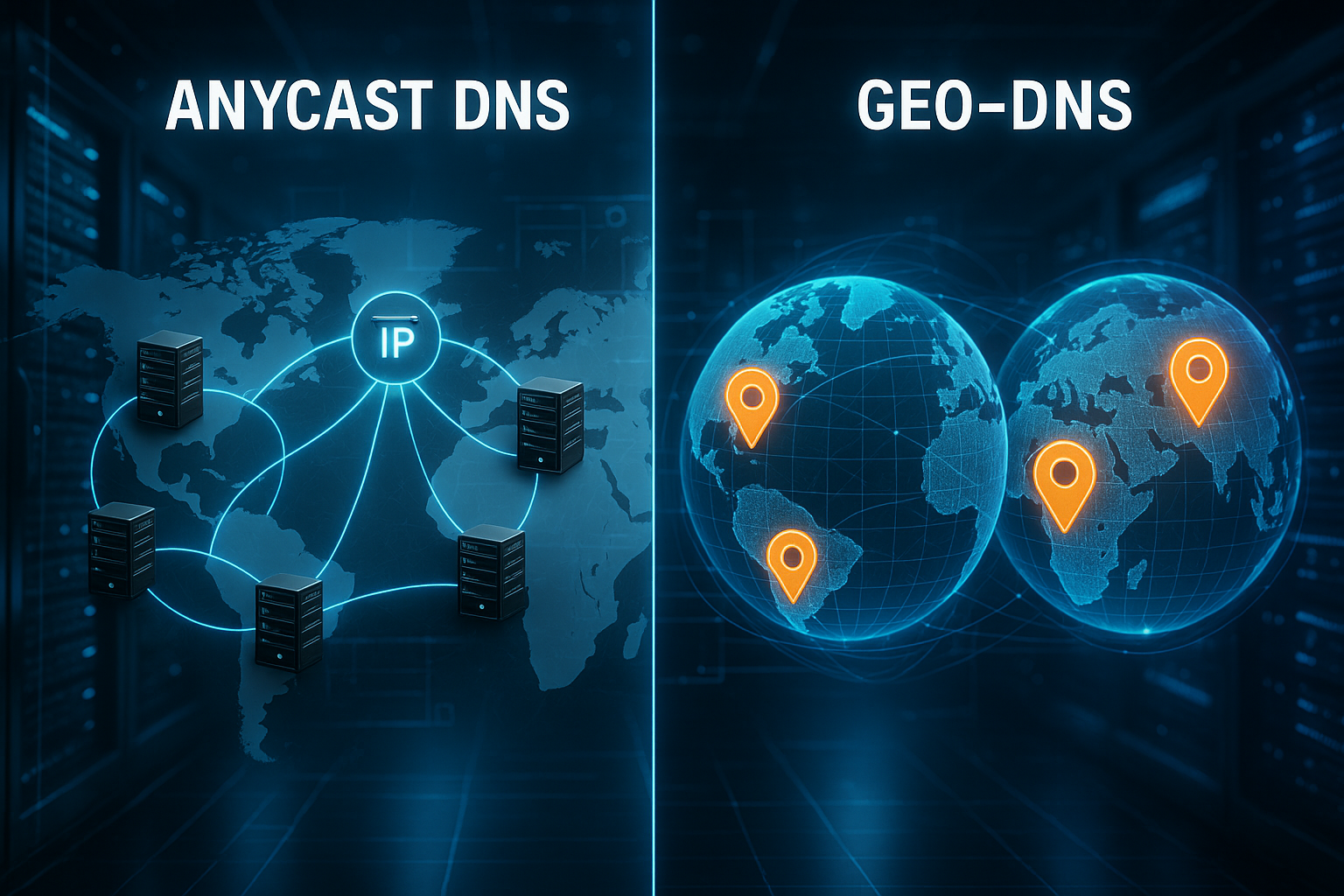
How Anycast DNS works
At Anycast multiple name servers share the same IP, and BGP automatically routes requests to the most accessible node. I benefit from this because users from every region get the shortest route. The Latency decreases, as no central server has to process all requests. If one location fails, the next node takes over without manual switching. This ensures that resolution and availability remain reliable even in the event of disruptions.
Larger anycast networks cover hundreds of cities worldwide, thereby reducing the Response time noticeable. The denser the network, the lower the latency dispersion across regions. I often see drops of double-digit milliseconds in monitoring data. Added to this is a natural DDoS-Advantage: Attacks are distributed across many nodes and lose their effectiveness. These characteristics make Anycast the standard choice for global traffic.
Geo-DNS in practice
Geo-DNS assigns requests to a specific server pool based on the source location. I use this to ensure that users in Germany receive German servers and content. This creates linguistic consistency, shorter paths to regional caches, and fulfills Data residencyRequirements. For campaigns, I can separate regions, perform A/B testing, and authorize load balancers per country. This allows regional differences to be clearly mapped.
The following remains important: Configuration. Geo-zones, IP-to-region mappings, and failover paths must be clearly defined. I pay attention to the TTL of the records, as this determines the switchover speed. For rollouts, I find it helpful to use shorter time-to-live values, which I increase again later; the guide to optimal DNS TTL Helpful benchmarks. With this discipline, routing and user experience remain predictable.

Anycast vs. Geo-DNS in direct comparison 2025
I make my choice based on Routing, latency, control, reliability, and maintenance. Anycast scores with automation and short paths without many rules. Geo-DNS impresses with targeted control, for example for language versions, regional prices, and laws. For global shops, I count every millisecond and therefore often rely on Anycast. If, on the other hand, I need clear country separation, I resort to geo rules.
| Aspect | Anycast | geo-DNS |
|---|---|---|
| routing principle | Automatic to the nearest/best node | Location-based via Region-Rules |
| Latency | Very low, without much intervention | Depending on configuration and distribution |
| Control | Little manual control required | fine-grained, more administration |
| Scaling | Very good worldwide | Good, but more administratively intensive |
| DDoS protection | Strong load distribution | Good, focus on regions possible |
| Reliability | Automatic redirection in case of failures | High with clean failover |
| Furnishings | Almost plug-and-play | Complex planning of the rules |
| Best use | Global sites with high traffic | Local content, laws, languages |
The decisive factor remains the Objective. For maximum performance and easy maintenance, Anycast pushes requests closer to users. For location-aware features, Geo-DNS provides the necessary rule base. Both can coexist and complement each other. This gives me flexibility without sacrificing speed. This combination has supported many product roadmaps over the years.
Performance values, latency, and reliability
I measure the Response time the DNS resolver across multiple continents and collect median and P95 values. Anycast typically reduces dispersion, which significantly lowers the P95. Geo-DNS offers advantages when I keep users in regional clusters. For failures, I plan health checks that remove faulty targets from the pool. This keeps the Accessibility even in the event of partial failures.
A second lever is the TTL. Short TTLs accelerate changes and failovers, but increase the number of requests. Long TTLs reduce the load on the infrastructure, but delay switchovers. I use staggered TTL strategies with prepared cutover windows. Monitoring alarms check the rate, NXDOMAINs, and servo codes. This allows me to detect anomalies early and respond proactively.
Security aspects, DNSSEC, and DDoS
I activate DNSSEC, to prevent manipulation of responses. Signed zones protect against spoofing and man-in-the-middle attacks. With Anycast, the signature chain remains consistent across all nodes. Geo-DNS requires clean signatures for each response variant to keep the chain valid. Regular rollovers The key and tests with validators belong in the operation.
Against DDoS I rely on multi-layered measures. Anycast distributes unwanted load and increases the capacity of the name servers. Rate limits, DNS cookies, and response padding make attacks even more expensive. I also check the ability to perform automatic blackholing. This ensures that the authoritative service remains deliverable even if individual vectors strike.
Hybrid architecture: rules plus automation
A hybrid of Anycast and Geo-DNS combines speed and controllability. I use Anycast to move the name servers closer to the users. At the same time, I define geo-rules for countries, languages, or partner zones. This structure shows its strength when compliance and speed matter. For the delivery level, I supplement this with Multi-CDN strategies and regional caches.
It is important to have a clear Priority the rules. Health checks decide first, geography second, and features such as weighted routing conclude. I document this cascade so that teams understand it. For releases, I plan stages that I can roll back if necessary. This keeps rollouts manageable, even during peak times.

Application scenarios and case studies
For global E-Commerce-shops, Anycast delivers the best balance between cost and profit. Every millisecond counts when it comes to conversion, and downtime costs revenue. Media portals combine geo-rules with Anycast to combine regional content and fast resolution. SaaS providers with data residency use Geo-DNS for country specifications and maintain performance with Anycast name servers. For the edge of delivery, I prefer Edge and CDN hosting in order to keep the distance to the end user short.
CDNs benefit greatly from Anycast, Because POP proximity brings direct latency advantages. Corporate portals with local languages rely on Geo-DNS to ensure that content is regionally appropriate. Gaming services need both: fast routing and regional session anchors. I respond to events such as sales or releases with temporarily shorter TTLs. After the peak, I raise them again to reduce load.
Provider selection and costs
I check the real thing Anycast-The provider's footprint and the density of locations. SLAs with clear uptime commitments and credits bring reliability to operations. Integrated DDoS protection reduces the risk of costly outages. DNSSEC support with easy key maintenance saves time. APIs, rollback functions, and change logs help me in my daily work.
At Costs I look at requests, zones, queries per second, and additional features. Free tiers help when starting out, but I factor in reserves for critical systems. In Europe, I plan budgets ranging from double digits to low triple digits per month, depending on traffic. Large platforms reach four-digit amounts, but quickly save money through fewer outages. I note hidden fees for DNSSEC or advanced routing in the comparison.

Operational tips for setup and operation
I start with clear Targets: Latency, error rate, time to change. Then I set up synthetic tests per region that measure DNS responses and end-to-end. For geo rules, I maintain IP region data and test edge cases. Health checks must be faster than the TTL, otherwise the failover will happen too late. I keep change logs clean so that I can quickly roll back configurations.
For Day 2 operations, the following applies Transparency. Dashboards display query rates, distribution, errors, and latency. Alerts respond to deviations beyond defined thresholds. I regularly conduct fire drills: targeted node shutdowns to verify failover. Documentation and runbooks help when things get serious. This ensures that the service remains reliable even under pressure.
Resolver behavior, caching, and TTL traps
I take into account the behavior of large Resolver (access providers, public DNS), because they shape the effectiveness of my strategy. Anycast determines which authoritative node responds, but the end user experiences the latency of the Resolver nearest POPs. If a company works with centralized egress, requests from branches often end up at a distant resolver—geo-mapping can then originate from the company headquarters instead of the user's location. I therefore evaluate catchments separately for user and resolver locations.
Caches bring speed, but they also hide TTL-Pitfalls. Some resolvers set TTL lower or upper limits, which means that very short or very long TTLs do not work as intended. Features such as serve-stale still deliver old responses in the event of authoritative failures – good for availability, but tricky in the event of urgent switches. I calibrate my TTLs so that failover targets are reliably reached, and test negative caches: NXDOMAIN responses are cached separately and can preserve misconfigurations for a surprisingly long time.
With Geo-DNS, I note that different users can run through the same resolver, which may be located in a different Region EDNS extensions for location proximity are not used everywhere for data protection reasons. I therefore plan conservatively: geo rules work with clusters instead of overly precise boundaries, and I document exceptions (e.g., border regions or roaming networks) to minimize mis-targeting.
IPv6, DoH/DoQ, and modern record types
I provide consistent dual stack-Strategy: A and AAAA receive equivalent targets, health checks test both protocols. Otherwise, imbalance leads to one-sided bottlenecks. Modern resolvers and browsers use Happy Eyeballs; slow IPv6 endpoints nevertheless worsen perceived latency. I therefore test IPv4/IPv6 separately and in combination.
Encrypted resolver protocols such as DoH and DoQ change paths and latencies, as requests can take new transit routes. Anycast remains useful, but catchments shift slightly. I measure end-to-end instead of focusing on individual hop times. In addition, I rely on HTTPS/SVCB-Records to signal to clients early on which endpoints and protocols are preferred. This shortens connection establishment and creates room for finer routing signals in the future.
At the top of the zone, I use ALIAS/ANAME or flattening to cleanly refer to CDN or geo targets despite apex restrictions. In doing so, I check how my provider flattens geo responses to avoid inconsistencies between chains. For services with many subdomains, I keep CNAME chains short to avoid additional resolver round trips.
Multi-provider authority and delegation
For high resilience, I plan multi-provider with authoritative DNS. Different NS in separate AS networks reduce systemic risks. I pay attention to consistent zone signing: key and algorithm selection must match across all providers. For rollovers, I coordinate KSK/ZSK across all platforms and test validations before flipping the switch.
With the delegation I carefully check glue records in the registry, delegation TTL, and DS entries. Changes to NS sets or DS take time to take effect worldwide. That's why I use stages: add new provider, check consistency, then remove the old one. For zone maintenance, I rely on hidden primary with AXFR/IXFR and NOTIFY. This prevents drift between providers and keeps the serial logic simple.
During operation, I evaluate the query distribution per NS IP. Imbalance indicates catchment anomalies or limits. I keep the number of NSs lean (typically 2-4 provider IPs) so that resolvers do not run into timeouts and retries increase latency.
Rollouts: Weighted, Canary, and Blue/Green
I roll changes with Weighted routing and Canaries Small percentages catch errors early on without disrupting many users. I combine geo rules with weights, for example to convert a country on a trial basis. For stateful backends, I plan session affinity outside of DNS—DNS itself is stateless and does not guarantee binding. Load balancers or tokens take over the sticking effects.
For Blue/Green I run two target worlds in parallel and switch via DNS cutover. Before the flip, I gradually lower the TTLs, then raise them again afterwards. Health checks run more frequently than the TTL so that exclusions take effect before caching. I also define degradation paths: it's better to temporarily disable a feature than to lose global traffic.
With Geo-DNS, I avoid rule explosion. I group countries with similar infrastructure, replace special rules with data models (e.g., price zones), and limit the number of active pools. This reduces maintenance effort and the margin for error.
Measurement and troubleshooting in practice
I rate Tail latencies (P95/P99) per region and compare them with catchment maps. Jumps indicate routing changes, overloaded POPs, or resolver retransmits. I attribute SERVFAIL and FORMERR spikes to DNSSEC errors, size limits, or defective responses. NXDOMAIN increases signal client bugs or typo campaigns; I use filters to separate legitimate and faulty queries.
To troubleshoot, I check the SOA-Serial per NS, compare signatures, and observe response sizes. Fragmentation can slow down UDP responses; if necessary, I activate TCP fallback metrics and EDNS tuning. Traceroutes to the anycast IP show which POP is currently serving—if there are deviations, I consider provider peering events.
Runbooks contain switches for serve-stale, deactivation of individual rules and emergency TTL sets. I maintain contact channels with providers and automate post-mortems: logs, metrics, change sets, and timelines are bundled into a package that quickly reveals the causes.
Compliance and data protection in concrete terms
I define which Log data where they are stored and how long they are stored. IP addresses are considered personal data; I clarify storage and pseudonymization with Legal. I document Geo-DNS decisions in a traceable manner: rules, sources of geo-data, and approvals. For Data residency I ensure that not only the app servers, but also caches, proxies, and telemetry remain in the permitted regions.
I use split horizon for internal and external views, but I keep an eye on the risks: mixed zones can quickly lead to inconsistencies. I strictly separate names (e.g., corp.example vs. public example) and prevent internal records from accidentally becoming public. Change approvals and the dual control principle are not a luxury here, but a must.

Quick overview: Which option should I choose?
I reach for Anycast, when global performance, low maintenance, and reliability are the main priorities. For regional content, languages, and laws, I use Geo-DNS with clear rules. In many cases, I combine both and get speed plus control. This mix covers e-commerce, media, SaaS, and gaming well. The decisive factors remain metrics, clear goals, and a provider with broad coverage, strong SLAs, and good usability.



