DNS errors often lead to serious problems such as website downtime, incorrect email delivery or security vulnerabilities - and they can often be avoided. In this article, I will use practical examples to show you how to reliably identify and analyze DNS misconfigurations and fix them using suitable tools.
Key points
- Typical errorsOutdated entries, incorrect server addresses or non-propagated DNS records often cause problems.
- Diagnostic toolsNSLOOKUP, DIG and Online DNS Checker help to make sources of error visible.
- Error messagesNotes such as "DNS_PROBE_FINISHED_NXDOMAIN" indicate configuration errors.
- Caching & FirewallsLocal DNS caches and network protection mechanisms often block the correct resolution.
- Permanent protectionRegular checks and monitoring prevent recurring errors.

DNS configurations are considered the linchpin for keeping websites and email services running reliably. As DNS entries are essential, you should check them at regular intervals and ensure that all entries are correct, up-to-date and clearly defined. Even small typos in an A record, a forgotten MX record or a faulty TXT entry can have far-reaching consequences. This makes it all the more important to be aware of typical sources of error and to be able to rectify them quickly.
Typical causes of DNS misconfigurations
Incorrect DNS entries are often caused by small but serious carelessness. Outdated IP addresses or incorrectly set MX records are just a few of the classic pitfalls. Adding or changing records under time pressure also often plays a role. Administrators and website operators sometimes overlook the fact that changes are not or only partially replicated in all name servers.
Other common pitfalls can be observed in various areas. For example, an inadequate transfer process when changing providers can result in the new server not being correctly linked to the domain if old DNS entries remain activated. Similarly, unclear documentation often leads to incorrect subdomains or services being inadvertently linked during the next update, which in turn can lead to outages. If you also set the TTL (Time to Live) values carelessly, you risk unnecessary delays in propagation and troubleshooting.
- Incorrect A or AAAA entries refer to servers that no longer exist.
- Missing MX records ensure that no e-mails can be delivered.
- A identical CNAME on several subdomains leads to conflicts.
- Invalid SPF entries in the TXT record favor spam filtering of legitimate mails.
These errors often occur when changing hosting or mail servers and are made even more difficult by a lack of documentation. If you would like to familiarize yourself with the basics, you will find a good introduction to How the DNS works. Timing also plays a major role: anyone expecting all servers worldwide to point to the correct IP addresses immediately after a DNS change, for example, may be disappointed. The global distribution and updating of the corresponding DNS data can take up to 48 hours.
Diagnostic tools: How to reliably detect DNS errors
I prefer to use command line tools such as NSLOOKUP under Windows or DIG under Linux/macOS - they quickly provide information about DNS entries and their integrity. These tools are particularly popular with administrators, as they are flexible and can be used independently of graphical user interfaces. Tip: NSLOOKUP and DIG can also be easily integrated into scripts to carry out automated checks.
This is how a typical check works:
nslookup -querytype=MX example.enThe command shows which mail servers are responsible for the domain. This is particularly helpful if users complain about email addresses not working. DIG provides additional details, for example in the event of problems with PTR records:
dig example.de ANYDNS tracing tools also enable location-based checks. This allows me to identify whether only users from one country are affected, for example. Depending on the error, I use DNSChecker, Constellix or the DNS Propagation Checker, among others. This question of location is highly relevant, especially in companies with an international focus, as a complete service can fail in certain regions without functioning resolution.

Example error messages and what they mean
Error messages in the browser or mail client provide valuable information about the cause of the error in the DNS system. A careful analysis is worthwhile in order to localize the problem more quickly. In some cases, these messages also help to identify firewalls or routing problems more quickly, as they can relate specifically to DNS connections. Here are the most common ones:
| Error message | Possible cause |
|---|---|
| DNS server does not respond | DNS server not available, firewall blocked |
| DNS_PROBE_FINISHED_NXDOMAIN | Domain not yet propagated, missing record |
| Timeout for DNS resolution | Incompetent server, routing problem |
| Mail cannot be delivered | MX or SPF errors in DNS records |
Straight DNS_PROBE_FINISHED_NXDOMAIN is a classic and can cause confusion if the domain is actually registered correctly. The DNS propagation check mentioned above often helps here to ensure that the DNS entries are transferred correctly worldwide. In addition, you should always check whether you are using the correct spelling of your domain and subdomain to rule out typing errors.

Troubleshooting checklist: step by step
I always start with simple tests and work my way deeper into the configuration if necessary - efficiently and comprehensibly. It is important to clearly record the results of each step so that you don't repeat the same steps several times when troubleshooting. Documentation for the whole team is also essential to prevent misunderstandings later on.
- NSLOOKUP and DIG locally to check A, MX and CNAME records.
- Online tools such as DNSLookup or MxToolbox supplement the check.
- Check synchronicityAre the details in the registrar, hosting panel and name server identical?
- Wait for propagation: After changes it can take up to 48 hours.
- Delete DNS cache:
ipconfig /flushdns(Windows)sudo dscacheutil -flushcache; sudo killall -HUP mDNSResponder(macOS)
A systematic approach is essential to avoid working in several places at the same time and then risking a loss of overview. This ensures that every change to the DNS is specifically monitored and validated. If you use a version system for your configuration files, you can quickly track which entries were changed and when. Combining DNS changes with a change management process also reduces the risk of accidental incorrect entries.
Configure DNS entries correctly in the WordPress environment
I often see website operators relying on automatic DNS settings and thus unintentionally transferring incorrect data. Better: targeted control. Especially in the WordPress environment, where many hosters offer preconfigured DNS settings, it is worth checking manually whether all records match the installed WordPress instance. This applies to subdomains, for example for development environments or staging systems, as well as additional services such as email, analytics or CDN services.
Almost all entries such as A, MX, CNAME and TXT can be edited in the hosting panel or via WordPress dashboards. Anyone working with IONOS will find helpful information on this in the DNS guide for IONOS. It is also important to regularly check whether WordPress plugins (e.g. for SMTP or security functions) require additional DNS entries. For example, many security plugins recommend separate TXT entries in order to use certain authentication mechanisms (such as DMARC).

Monitoring and best practices for safeguarding
Regular checks are crucial after every correction. To do this, I use tools that automatically monitor and report DNS changes. Such monitoring mechanisms are not only useful for large companies, but also for smaller projects. In the long term, this prevents entries from remaining outdated unnoticed or internal server names from being accessed by mistake.
These tools include both simple DNS monitoring services and comprehensive platforms that keep an eye on the entire network. For example, they check at fixed intervals whether a DNS record still corresponds to the stored IP, whether certain subdomains can be reached and whether MX records are responding correctly. If deviations are detected, you can be notified automatically by email or text message. This allows you to prevent potential failures at an early stage.
You should check this regularly:
- Documentation maintain all DNS records centrally
- Redundant name servers set up (e.g. secondary server)
- Monitoring Integrate with notification function
- Avoid dependencies to external resolvers
Reliable service providers such as webhoster.de offer comprehensive DNS monitoring features and are also leaders in terms of support:
| Provider | DNS-Check Tools | Automatic monitoring | Support |
|---|---|---|---|
| webhoster.de | Yes | Yes | excellent |
| Provider B | Yes | restricted | good |
| Provider C | no | Yes | average |
Another important aspect is the establishment of DNSSEC (Domain Name System Security Extensions). This allows you to prevent attackers from infiltrating fake DNS entries. DNSSEC ensures that the resolver can check whether the response to a DNS query is unchanged. Many providers already support DNSSEC, so you can activate it in your panel. However, careful configuration is required to ensure that the signing process works smoothly.
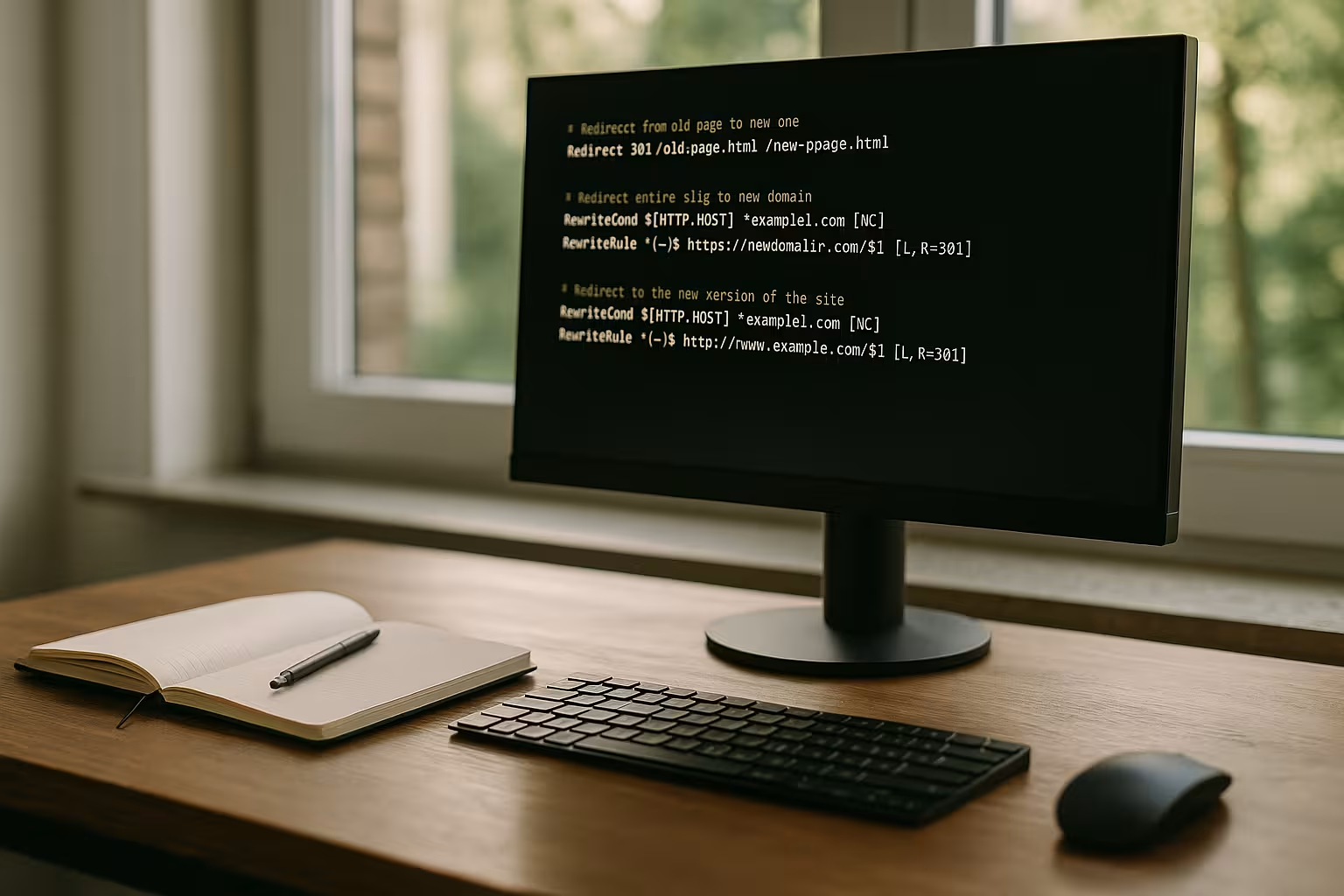
Typical case studies from practice
When moving a website, DNS changes are often not applied correctly. In one case, the A-record still pointed to the old server - even though all data had already been migrated. After a WHOIS query, I was able to identify and correct outdated name servers.
Another example: A newly set up mail server remained inoperable. Cause: MX record was missing and the associated SPF record was incorrectly formatted. Especially when sending emails, this can lead to messages either not arriving at all or being rejected as potential spam. SPF, DKIM and DMARC should therefore be set up correctly and checked regularly - especially if IP addresses or server names change.
Also very common: A customer set up a new domain and was surprised by the error message "DNS_PROBE_FINISHED_NXDOMAIN". The domain was registered correctly, but the CNAME record pointing to the actual web server was missing. What initially looked like a simple typo turned out to be a missing redirect. In such a case, it is sufficient to enter the correct CNAME record, but without the right diagnostic tools and prior knowledge, solving the problem often takes a long time.
We also encounter situations with accidentally created wildcard subdomains (such as *.example.com) that answer the resolutions for non-existent subdomains. This can not only trigger traffic loops, but also create security vulnerabilities. Such cases illustrate how important it is to have a clear concept in the DNS so that only explicit subdomains are authorized. A periodic audit of the DNS zone can help here.

Another practical step is to get to grips with advanced DNS functions. Especially when hosting multiple domains or different services (e.g. SaaS solutions, online store, external payment processing), it may be necessary to make targeted delegations. This means that individual subdomains are referred to other name servers, which are then responsible for the relevant service. Errors in this delegation can easily lead to parts of the website no longer being accessible.
It is also worth thinking about whether very short TTL values really make sense - although they speed up the transfer of changes, they can also be detrimental to performance if countless DNS queries are made each time a page is called up. A balance between flexibility and performance is often the best approach in practice.
Future-proof through error prevention and precaution
Avoiding DNS misconfigurations means constant learning, careful maintenance and the use of smart tools. If you work systematically, you retain control over all relevant DNS entries and ensure permanently secure accessibility. As modern websites are often closely interlinked with external services such as content delivery networks, email providers or analytics tools, you must always keep an eye on your own DNS as a central control element.
I regularly check all relevant DNS records using automatic queries and notification systems and document every change - this saves a huge amount of time in the event of an error. If you keep well-maintained DNS documentation, you can quickly revert to the original configuration in the event of a failure or make any necessary changes. A good system relies on transparency and traceability so that it is clear who makes which changes and when.
Also a Correctly set DNS redirect can be crucial when domains are merged or redirected. If such settings are entered incorrectly, there is a risk of SEO losses and a drop in visitor numbers. Duplicate content or inconsistent redirects have a negative effect on the ranking and can also confuse users. With a uniform URL concept and corresponding DNS redirects, you can avoid such problems in the long term.
If you familiarize yourself with the intricacies of the DNS at an early stage, you will be able to avoid common mistakes in advance. When registering a domain, you should already be aware of which DNS entries are absolutely necessary: A/AAAA for the main site, CNAME for subdomains and MX for receiving emails often form the basic framework. Additional TXT records such as SPF, DKIM or DMARC increase email security and should be set up in consultation with the respective provider at an early stage.
Ultimately, a forward-looking DNS configuration pays off in many ways: Visitors can reach websites securely and with high performance, emails land reliably in the inbox and internal IT processes run smoothly. Those who also use monitoring and DNSSEC minimize the risk of outages and data protection problems. This means that DNS is not just an invisible backbone, but a strategic factor for stability and success in online business.



