The multi-tier architecture separates web applications into clearly delineated tiers and thus enables plannable Scalinghigh Security and efficient operation for growing traffic profiles. I will show you the structure, hosting requirements and useful additions such as caching, messaging and gateways so that your project runs reliably and cost-effectively.
Key points
Before I go any deeper, I will summarize the most important guidelines that should underpin any multi-layer architecture. Each layer has its own task and can be expanded separately. This allows me to minimize risks, isolate errors more quickly and control costs in a targeted manner. With clean network separation, I secure confidential data and keep attack surfaces to a minimum. Tools for monitoring, automation and restart times ensure that services remain reliable and that the Performance even under load. These principles form the framework within which I make decisions on Infrastructure and technology selection.
- Separation of the layers: UI, logic, data
- Horizontal Scaling per animal
- Network-Segmentation and WAF
- Caching and messaging for speed
- Monitoring and recovery processes
What is a multi-tier architecture?
I divide the application into logically and physically separate layers so that each layer can be scaled and secured in a targeted manner. The presentation layer answers user requests and takes care of initial validation so that unnecessary load does not reach the backends. The business logic processes rules, rights and workflows and keeps itself stateless in order to distribute the load evenly and to be able to start new instances quickly. Data management focuses on integrity, replication and backups so that I can keep data consistent and available. If required, I can add additional services such as gateways, caches or queues to reduce latency and optimize the Decoupling of the components. This keeps dependencies manageable, and I regulate the Performance per part.

Structure: Shifts and tasks
In the presentation layer, I rely on clean APIs and a clear separation of presentation and data so that frontends remain maintainable and load quickly. The business logic bundles rules, accesses external services and checks rights, which allows me to keep the access paths consistent. I keep this level stateless so that the load balancer can distribute requests flexibly and new instances take effect immediately in the event of load peaks. In data storage, I prioritize replication, high availability and encryption so that the Confidentiality is maintained and recoveries can be planned. In addition, I take read and write patterns into account in order to select suitable databases and to optimize the Latency low.
Additional tiers: caching, messaging, gateways
I add caching for semistatic content, session data or frequent queries, thereby significantly reducing the load on the database. Messaging via queues or streams separates slow tasks (e.g. report generation) from the user flow, allowing the user to receive quick responses. API gateways bundle interfaces, enforce policies and facilitate observability across services. A reverse proxy in front of the web tier helps with TLS, routing, compression and protects internal systems from direct access; I summarize the details in this article on the Reverse proxy architecture together. With these building blocks, I increase the Efficiency communication and minimize Load on core systems.

Hosting requirements: Infrastructure
I place each layer on separate instances or in separate logical environments for finer control over scaling and security. Network segmentation via subnets or VLANs limits cross-traffic and reduces risks from internal attack paths. I place a load balancer in front of the application tier, which distributes connections, performs health checks and favors zero-downtime deployments; a practical overview is provided by the Load balancer comparison. For automatic scaling, I define clear metrics such as CPU, requests per second and response time so that rules work properly. Infrastructure as code ensures reproducible setups so that I can provide environments identically and Error recognize early on what the later Maintenance simplified.
Hosting requirements: Security
I place firewalls and a WAF in front of the front ends so that typical attacks are blocked at an early stage. Strict guidelines only allow data storage connections from the application tier and deny any direct internet access. I encrypt data at rest and during transmission, which meets compliance requirements and makes leaks more difficult. Regular backups with clear retention periods and tested recovery protect against failures and accidental deletions. Supplementary network security groups allow fine-grained rules so that only necessary Traffic flows and the attack surface minimal remains.
Hosting requirements: Operation and automation
Monitoring covers system resources, service health, business KPIs and latencies so that I can spot trends and outliers in good time. I centralize logs and metrics, link correlations and thus shorten the time to root cause. Automated deployments with Blue-Green or Canary reduce risk and allow fast rollback. For reliability, I plan active replication, quorum mechanisms and restart scripts, which I test regularly. In this way, I ensure that services react in a controlled manner even under load and that the Availability remains high, while Expenditure in the company.
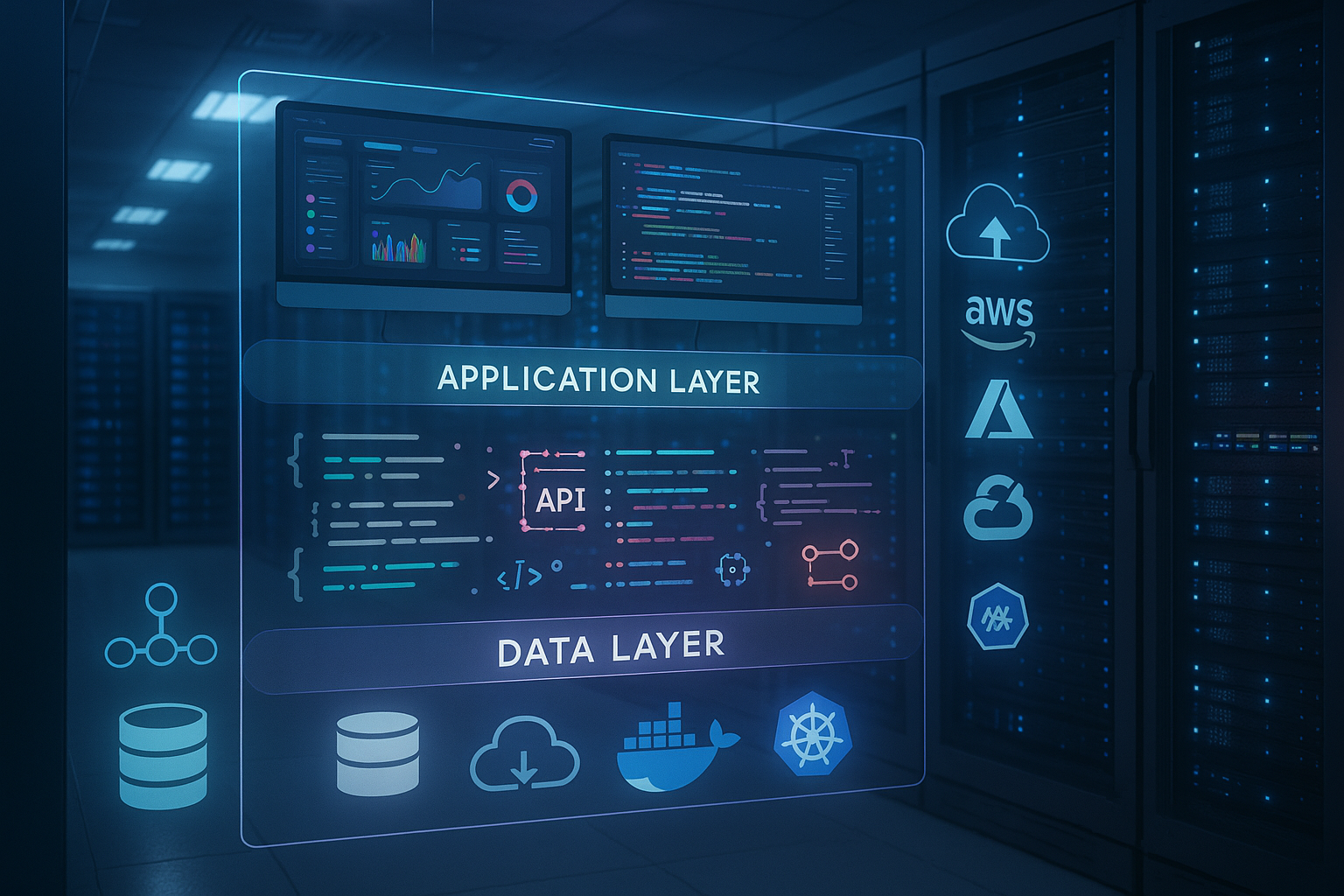
Cloud, on-premises and hybrid
I choose the platform based on compliance, latency requirements and cost model. Cloud services score points with managed offerings for databases, caches or queues, which reduces time-to-value. On-premises provides maximum control over data locations, hardening and networks, but requires more in-house expertise. Hybrid scenarios combine both, such as sensitive data storage on site and elastic computing load in the cloud. It remains important to plan architectures in a portable way in order to avoid lock-in and to ensure the Flexibility for future Requirements to preserve.
Data model and persistence strategies
The data tier benefits from a conscious selection of storage technologies: Relational databases deliver ACID transactions and are suitable for consistent workflows, NoSQL variants show their strengths with large, distributed read accesses and flexible schemas. I check read/write ratios, data volume, relationship density and consistency requirements. For scaling, I combine read replicas, partitioning or sharding and plan indices specifically along critical queries. I keep write paths short and rely on asynchronous ancillary work (e.g. search index updates) via queues to keep response times low. I regularly test backups as recovery exercises; I also verify replication delays and ensure that restore times match my RTO/RPO targets.
Consistency, transactions and idempotency
Distributed workflows are created between tiers and services. I prioritize explicit transaction boundaries and use patterns such as Outbox to publish events reliably. Where two-phase commits are too heavy, I rely on eventual consistency with compensation actions. I add exponential backoff and jitter to retries and combine them with timeouts and idempotency keys so that double processing does not generate any side effects. I plan unique request IDs in the API design; consumers save the last processed offset or status in order to reliably recognize repetitions.
Caching in detail
Caching only works with clear strategies. I differentiate:
- Write-through: Write accesses end up directly in the cache and in the database, consistency remains high.
- Write-back: The cache absorbs the write load and writes back with a delay - ideal for high throughputs, but requires robust recovery.
- Read-through: The cache fills itself from the database as required and retains TTLs.
Messaging semantics and concurrency
Queues and streams carry workloads, but differ in delivery and ordering. "At-least-once semantics are standard, so I design consumers to be idempotent and limit parallelism per key where order matters. Dead-letter queues help to handle faulty messages in isolation. For longer tasks, I use heartbeats, visibility timeouts and status callbacks so that the user path remains reactive while backends process stably.

API design, versioning and contracts
Stable interfaces are the backbone of a multi-tier architecture. I establish clear contracts with schema validation, semantic versioning and backward compatibility via additive changes. I communicate deprecations with deadlines and telemetry to identify active users. API gateways enforce authentication and rate limits, transform formats and strengthen observability via request and trace IDs. For front ends, I reduce chattiness with aggregation or BFF layers so that mobile and web clients receive tailored responses.
Security in depth: Secrets, keys and compliance
I store secrets in a dedicated secret store, use short lifetimes and rotation. I secure key material via HSM/KMS and enforce mTLS between internal services. Least privilege access models (role-based), segmented admin access and just-in-time rights reduce risks. A WAF filters OWASP top 10 attacks, while rate limiting and bot management curb abuse. I embed regular patch and dependency management in the process and document measures for audits and GDPR verification - including deletion concepts, encryption and access paths.
Resilience: timeouts, retries and circuit breakers
Robust services set clear time budgets; I define timeouts per call along the entire SLO and only use retries for truly temporary errors. Circuit breakers protect downstream systems, bulkheads isolate resource pools, and fallbacks provide degraded responses instead of complete failures. Health checks not only check "is the process alive?", but also dependencies (database, cache, external APIs) in order to redirect traffic in good time.

Scaling, capacity and cost control
I plan capacity along measurable seasonality and growth rates. I combine auto-scaling reactively (CPU, RPS, latency) and predictively (schedules, forecasts). I keep an eye on costs with tagging, budgets and alerting; architectural decisions such as cache hit ratio, batch windows and storage levels directly influence the calculation. For stateful systems, I optimize storage classes, IOPS profiles and snapshots. Where vertical scaling is more favorable, I use it specifically before I distribute horizontally.

Deployments, tests and migrations without downtime
In addition to Blue-Green and Canary, I use feature flags to activate changes step by step. Ephemeral test environments per branch validate infrastructure and code together. For databases, I use the expand/contract pattern: first add new fields and write/read dual, then remove old fields after migration. Shadow traffic makes effects visible without affecting users. I plan rollbacks in advance - including schema and data paths.
Multi-region, DR and latency
For high availability targets, I distribute tiers to zones/regions. I define clear RTO/RPO, decide between active/active and active/passive and check replication delays. Geo routing and near-user caches shorten paths, while write conflicts are resolved using leader-based or conflict-free strategies. I keep DR runbooks up to date and practice them regularly so that switchovers remain reproducible.
Best practices for development and hosting
I keep the application tier stateless so that scaling works without friction and failures do not lose any sessions. Asynchronous communication via queues decouples subsystems and reduces response times in the user path. Frequently used data ends up in the cache, allowing the database to cope better with load peaks. Network segmentation per tier closes unnecessary paths and strengthens control options. Seamless observability with metrics, logs and traces shortens troubleshooting and creates a reliable Base for continuous Optimization.
Challenges and solutions
Multi-layered systems require additional coordination, especially when it comes to interfaces, deployment and access rights. I address this with clear contracts between services, repeatable pipelines and clean documentation. Containers and orchestration standardize deployments, increase density and make rollbacks plannable. For service-like architectures, it is worth taking a look at microservices variants; this article on Microservices Hosting. With regular security checks and recurring recovery tests, I keep risks to a minimum and protect the environment. Availability and Quality.
Monitoring, logging and tracing
I not only measure infrastructure metrics, but also link them to business signals such as orders or active sessions. This allows me to recognize whether a peak is healthy or indicates an error. Tracing across service boundaries makes slow hops visible and facilitates prioritization in tuning. Central logs ensure context by establishing correlations via request IDs and time windows. This creates transparency across the entire chain and allows me to Causes insulate faster and Measures in a targeted manner.
SLOs, alerting and operational readiness
I define service level objectives for availability and latency, derive error budgets from them and manage releases accordingly. I trigger alerts based on symptoms (e.g. on user error rates and p95 latencies), not just on host metrics. Runbooks, postmortems and guard rails for incident response consolidate operational maturity. I consolidate metrics, logs and traces into dashboards per tier and add synthetic tests to continuously test end-to-end paths.

Multi-tier hosting: provider & selection
When choosing, I look for clear SLAs, response times in support and real scaling options without hard limits. A transparent price structure prevents nasty surprises during peak loads. I also check whether logging, tracing, backups and security modules are integrated or generate additional costs. In comparative tests, a provider that supports multi-tier setups with strong automation, high availability and a good price-performance ratio stands out. The following table clearly summarizes the core criteria so that you can quickly make a reliable decision. Decision for your Project meet.
| Provider | Multi-tier hosting | Scalability | Security | Price-performance | Special features |
|---|---|---|---|---|---|
| webhoster.de | Yes | Excellent | Very high | Top | German service, support |
| Provider B | Yes | Good | High | Good | – |
| Provider C | Partial | Medium | High | Medium | – |
In practice, the combination of automatic scaling, integrated security and reliable support pays off. Those who grow quickly benefit from on-demand resources without having to rebuild the architecture. Teams with compliance requirements value traceable processes and audits. I therefore always check how well the provider maps multi-tier concepts such as segmentation, replication and gateways. This is the only way Costs calculable and the Performance consistent.

Summary: What you take with you
The separation into tiers creates order, increases security and opens up scalable options for growing projects. Additional components such as caches, queues and gateways reduce latency and keep workloads cleanly separated. Appropriate hosting with segmentation, automatic scaling and integrated observability makes operations predictable. I recommend an architecture that remains portable so that decisions on cloud, on-premises or hybrid are open in the long term. With consistent automation and clear processes, you can keep an eye on costs and ensure the Quality and the Resilience your application.



