I will show you how to Monitor server utilization and identify bottlenecks in real time before visitors bounce. I rely on concrete tools, clear metrics and practical measures that make modern hosting environments measurable. relieve.
Key points
- Core metrics at a glance: CPU, RAM, I/O, network
- Real-time alerts and trend analyses for Vorsprung
- Toolmix from cloud, agents, open source
- Scaling with load balancing and caching
- Automation and AI-supported forecasts

What does server utilization really mean?
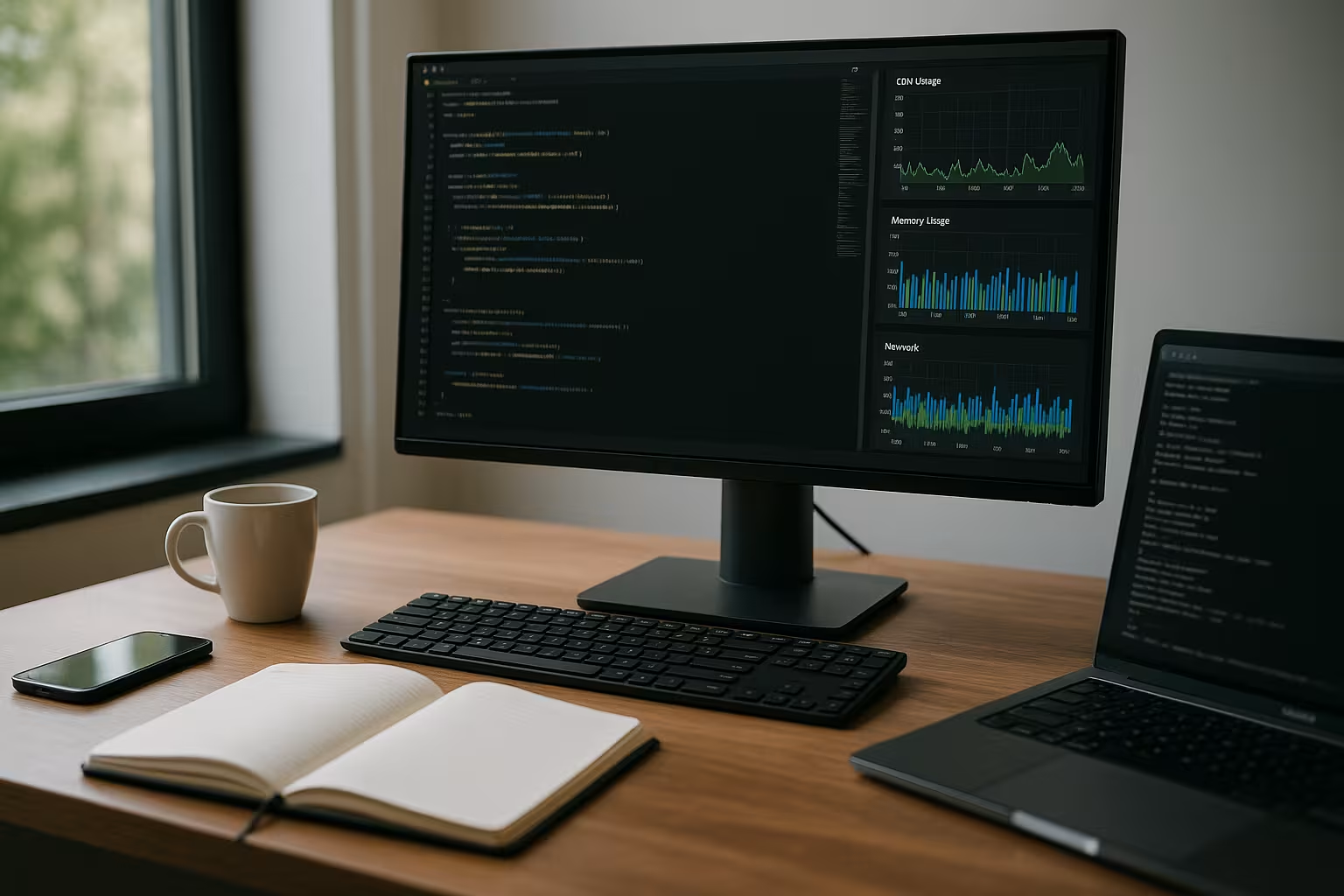
I understand utilization to mean the sum of all active Resourcesthat a server requires for applications, processes and accesses. CPU time, RAM, hard disk I/O and network latency all play a decisive role. A single bottleneck is enough to slow down entire workloads. I evaluate these key figures together and assess them in the context of the workload. This allows me to recognize whether an application is slowing down, a service is hanging or the traffic is exceeding the System overruns.
Read core metrics correctly
I always check CPU load peaks with load average and process queues to separate real bottlenecks from short peaks and to minimize the Capacity to assess. For RAM, free pages, page caches, swap activity and OOM killer events count. For storage, I focus on IOPS, latencies, queue depth and read/write rates. In the network, I pay attention to bandwidth, retransmits, packet loss and unusual ports. Only the correlation of these values shows me the actual cause and saves valuable time. Response time.

Tool overview and selection
For reliable monitoring, I rely on a combination of agents, remote queries and Dashboards. Agents provide deep host metrics in real time, while remote sensors check services such as HTTP, DNS or databases. APIs, a clean alerting workflow and good reporting functions are important. I also evaluate costs, depth of integration and scalability. Tools must make the metrics usable, otherwise monitoring remains superficial.
| Place | Tool | Highlights | Suitable for |
|---|---|---|---|
| 1 | webhoster.de | Comprehensive monitoring, hosting integration, intuitive dashboards | Websites, WordPress, scaling projects |
| 2 | Paessler PRTG | Versatile sensors, clear surfaces | Hybrid environments, Windows/SNMP focus |
| 3 | SolarWinds SAM | App/server monitoring, powerful reports | Enterprise teams, on-premises |
| 4 | Datadog | Real-time analysis, many integrations | Cloud-native, Container/Kubernetes |
| 5 | Checkmk | Scalable open source monitoring | Linux hosts, various plug-ins |
| 6 | Dynatrace | AI analyses, full stack, auto-discovery | Large landscapes, microservices |
I like to use a clear checklist with criteria such as coverage, TCO and alert quality for the selection and refer to this compact Monitoring guide for a quick start. This allows me to make well-founded decisions and prevent a tool from being used later on. limited.
Open source alternatives with depth
If you want full control, use Zabbix, Icinga 2 or LibreNMS and gain flexible Adjustments. I rely on modular pollers, my own checks and defined alarm paths. Open source saves license costs, but requires clear responsibilities and maintenance. Playbooks and IaC templates keep setups reproducible and secure. With structured dashboards and role rights, I also guide large teams effectively through the Monitoring.

Integration and automation in everyday life
I connect hosts and services via API so that new systems can be automatically visible can be used. Home Assistant in combination with linux2mqtt collects Linux metrics via MQTT and displays them in individual dashboards. I send alerts as a push, mail or webhook as soon as threshold values are exceeded. For readiness, I bundle alerts with PagerDuty and ensure clear escalation chains. Only automated reactions transform raw data into real Availability.
Immediate measures for peak loads
I first clean up temporary files and close hanging files. Services. I then postpone automatic updates until quieter times and check cron jobs. An orderly restart reduces leaks and resets broken processes. I increase system-related limits such as file descriptors, worker processes and PHP FPM queues. With these steps, I gain distance from the peak and buy time for sustainable Optimization.

Application optimization: caching and database
I use Redis as an object cache and reduce the load on databases through efficient Hits. Varnish accelerates static and cacheable content before the web server. In SQL, I check slow queries, missing indices and inaccurate sorting. Connection pools stabilize peaks, query hints prevent expensive full scans. Every second that the app calculates less gives capacity for real work. Traffic.
Scaling with load balancer and cloud
I distribute requests via load balancers and hold sessions with cookies or centralized Storage. Horizontal scaling increases the number of workers in parallel and reduces waiting times. Vertically, I add CPUs, RAM or NVMe storage for I/O-heavy workloads. In the cloud, I combine auto scaling, snapshots and managed services for rapid adjustments. Hosting offers such as webhoster.de give me predictability and technical flexibility. Freedom.
Forecasting and capacity planning
I use long-term metric series to visualize trends. make. Seasonal patterns, releases and marketing peaks send clear signals. I use forecasts to determine CPU, RAM and I/O reserves that intercept real peaks. AI-supported models detect anomalies before users notice them. I offer an introduction with this compact AI predictionthat will help me make decisions for the next Quarter facilitated.
Targeted relief for WordPress
I minimize plugin ballast, activate OPcache and place Full-Page-Cache before PHP. Image optimization, HTTP/2/3 and Brotli compress the data paths. Object cache with Redis reduces database hits in the millisecond range. Heartbeat intervals and cron control reduce the load on shared hosts. For a structured roadmap, please refer to the Performance guidemy tuning steps bundles.
Clearly define service level targets
I translate technology into reliable Service Level Indicators (SLI) and Service Level Objectives (SLO) so that teams know what "good" means. Instead of just reporting CPU percentages, I measure p95/p99 latencies, error rates, availabilities and Apdex. My SLOs are based on the business: a store needs short checkout latency, a CMS needs stable editorial workflows.
- SLIs: p95 latency per endpoint, error rate (5xx), uptime per region, queue latency, DB commit latency
- SLOs: e.g. 99.9% uptime/month, p95 < 300 ms for start page, error rate < 0.1%
I define error budgets that clearly state how much deviation is tolerable. If budgets are used up, I pause risky deployments and prioritize stability over new features.
Alert design without alarm fatigue
I structure alerts according to severity and impact. Instead of individual threshold values, I use dependent alerts: if the app availability drops, I first check the network and database before reporting CPU noise. Deduplication, time windows (p95 over 5 minutes) and hysteresis prevent fluttering.
- Routes: Critical to standby, warnings in the team chat, information in the ticket system
- Maintenance windows and quiet hours: planned work does not disrupt the on-call schedule
- Auto-Remediation: execute log rotation and cache clearing when disk usage is full
Each alert in Runbooks refers to specific Next steps and ownership. This is how I measurably shorten MTTA and MTTR.
Observability in practice: metrics, logs, traces
I combine metrics with logs and traces to see causes instead of symptoms. Correlation IDs move through web server, app, queue and database so I can trace a slow request to the record. Log sampling and structured fields keep costs and Signal in balance.
I use eBPF-supported system profilers to analyze kernel-related hotspots (syscalls, TCP retransmits, file locks) without adapting the app. Traces show me N+1 problems, chatty services and connection pools that are too small. This is how I discover whether there is a bottleneck in the code, in the infrastructure or in Dependencies stuck.
Containers and Kubernetes under control
I measure at node, pod and namespace level. CPU throttling, memory limits and OOMKilled events reveal whether requests/limits fit. I check p95 latency per service, pod restarts, HPA triggers, cubelet health, cgroup printing and network policies.
Deployment strategies (Blue/Green, Canary) relieve peaks. Readiness/liveness probes are configured consistently so that replicas rotate out of the load balancer in good time. For stateful services, I monitor storage classes, volume latencies and Replica-Lag in databases.
Tests: Synthetic, RUM, Last and Chaos
I combine synthetic checks (login, checkout, search) from multiple regions with real user monitoring to see real experiences and edge cases. Before large campaigns, I run load tests with realistic data and scenarios, identify tipping points and set scaling rules.
Targeted chaos experiments (service failure, network latency, database failover) test resilience. A clear security framework is important: strictly limited experiments, fallback plan and monitoring alarm paths that aware may be triggered.

Industrial hygiene: Runbooks, On-Call, Postmortems
I keep runbooks short and easy to implement: diagnostic commands, dashboards, restart commands, escalation. On-call roles are clear, including substitution and rotating on-call duty. After incidents, I carry out blameless postmortems with a timeline, root cause analysis (5 Why) and specific actions - including deadline and owner.
I actively control metrics such as MTTR, change failure rate and time to detection. This makes stability a team routine and not a coincidence.
Cost and data strategy: retention, cardinality, TCO
I plan data retention consciously: I keep fine-grained metrics for 14-30 days, condensed metrics for 90-365 days. Logs are sampled according to relevance and stored PII-free. I avoid high label cardinality (e.g. no session IDs as labels) in order to minimize storage and queries. slim to hold.
I keep TCO transparent with cost budgets per team and workload. Dashboards show costs per request, per service and per environment. This allows me to document measures such as caching, right-sizing or the removal of unnecessary metrics in euros.
OS and network tuning with a sense of proportion
I set the CPU governor and IRQ distribution to match the workload, pay attention to NUMA and pin critical interrupts. For memory-intensive apps, I check Huge Pages, Swappiness and Transparent Huge Pages - always validated with benchmarks, not by instinct.
In the network, I adjust TCP buffers (rmem/wmem), backlogs, conntrack limits and keepalive intervals. Clean time sources (Chrony/NTP) prevent drift - important for TLS, logs, traces and Replication. A local DNS cache reduces latency peaks in day-to-day business.
Security and compliance in monitoring
I keep agents minimally privileged, rotate access keys and consistently encrypt transport routes. Certificates have fixed terms, offboarding is part of the deployment. I mask PII (e.g. email, IP) in logs, enforce retention policies and document access in an audit-proof manner.
Alerts also follow the principle of least privilege: only those who need to act see sensitive details. This keeps monitoring and data flow legally compliant and safe.
High availability and recovery
I define RPO/RTO for each service and back them up with real restore tests - not just backups, but complete restarts. For databases, I measure replica lag, test failover and verify that apps switch read/write paths cleanly.
Runbooks contain disaster scenarios (region down, storage defective) and clear communication paths to stakeholders. This means that operations can be planned even under stress and predictable.

Summary: From visibility to stability
I start with clear metrics, quick alerts and a Toolthat fits the environment. I then take the load off applications, scale them in a targeted manner and secure processes with automation. AI-supported forecasts give me time for planning instead of putting out fires. This keeps load times low, budgets predictable and teams relaxed. Keeping servers transparent prevents outages and turns monitoring into real work. Competitive advantage.



