Thread contention slows down web servers because threads compete for shared resources such as locks, caches, or counters, thereby blocking each other. I will show how this competition slows down web hosting performance explains the concurrency issues behind this and which practical countermeasures are reliable.
Key points
- Locks are bottlenecks: Synchronization protects data, but creates waiting times.
- schedulerLoad increases: Too many threads per core reduce throughput.
- RPS and latency suffer: Contention noticeably reduces requests per second.
- Event-driven Servers help: NGINX and LiteSpeed are better at bypassing blockages.
- Monitoring First: Prioritize goal metrics, evaluate contention only in context.
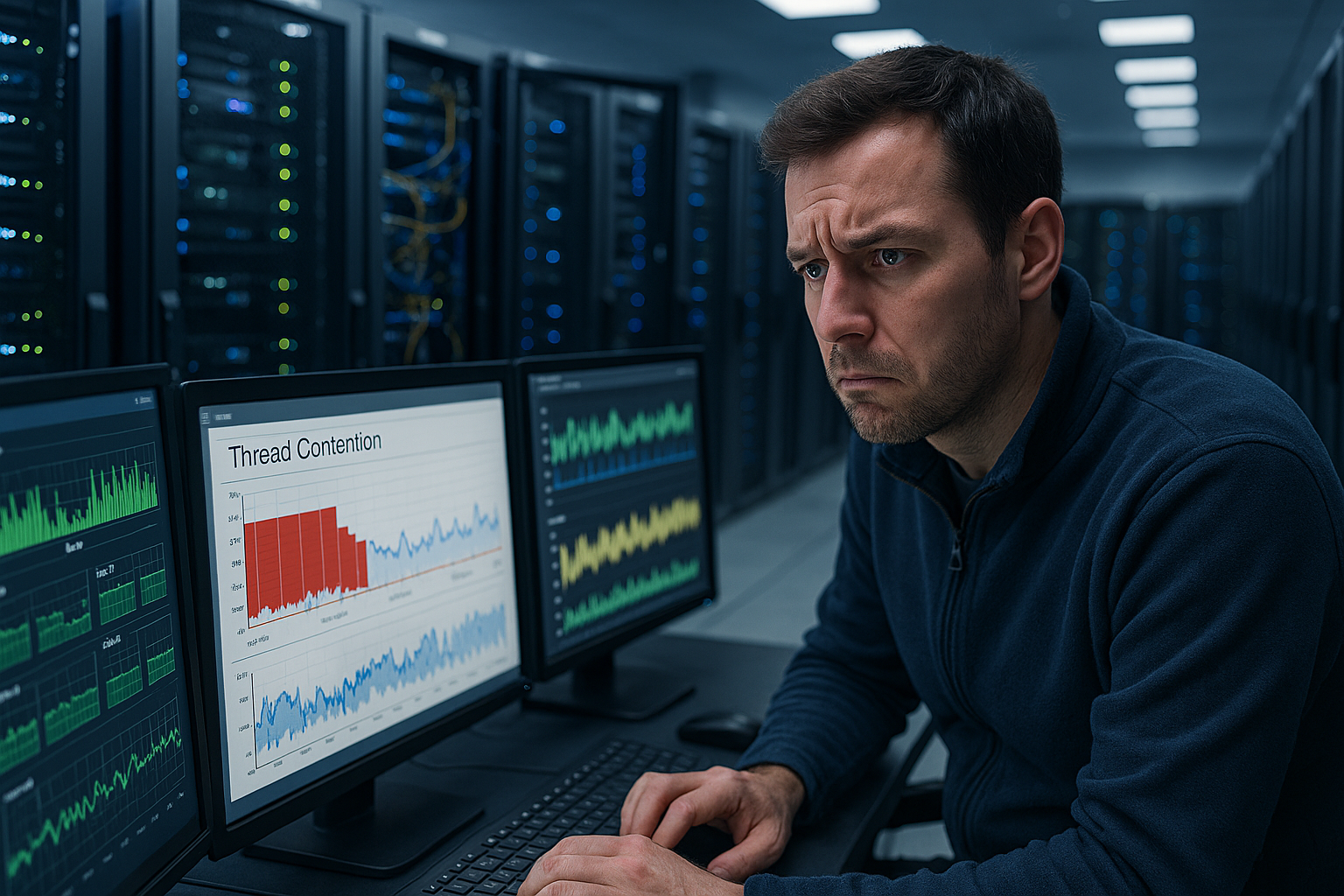
What triggers thread contention in the web server
I define Contention as competition between threads for synchronized resources such as mutexes, semaphores, or shared caches. Each thread has its own call stack, but often many requests access the same lock. This prevents data errors, but significantly increases waiting time. With dynamic page access, this is particularly common with PHP-FPM, database connections, or session handling. Under load, threads park in queues, which Latency increases, and throughput decreases.
A practical example helps: 100 users simultaneously start a dynamic query, all of them need the same cache key. Without synchronization, you risk race conditions; with synchronization, congestion occurs. I then see blocked threads, additional context switches, and growing run queues. These effects add up and put pressure on the RPS This pattern appears regularly in web server benchmarks [3].
Why contention kills response times and throughput
Too many waiting threads drive the CPU into unnecessary context switching. Each change costs cycles and reduces the effective work per unit of time. If scheduler pressure is added to this, the system tips into thrashing. I then observe non-yielding messages in SQL or PHP FPM pools and a hard collision of IO and compute paths [5]. The result is noticeably longer response times and fluctuating P95-Latencies.
In measurements, efficient servers are in the range of high thousands of RPS, while contention-plagued setups drop visibly [6]. The effect affects not only requests, but also CPU and IO paths. Even asynchronous components such as IO completion ports show an increasing contention rate without necessarily breaking overall performance – the context decides [3]. I therefore focus on goal metrics such as throughput and response time and always evaluate contention values in the overall picture. This approach prevents false alarms and draws attention to real Bottlenecks.

Measurable effects and benchmarks
I quantify Contention-Consequences with throughput, latencies, and CPU shares. The table shows a typical pattern under load: RPS drops, latency increases, CPU consumption climbs [6]. These figures vary depending on app logic and data path, but they give a clear direction. This overview is sufficient for me to make tuning decisions before delving deeper into code or kernel metrics. The decisive factor remains whether measures Response time reduce costs and increase throughput.
| Web server | RPS (normal) | RPS (high contention) | Latency (ms) | CPU usage |
|---|---|---|---|---|
| Apache | 7508 | 4500 | 45 | High |
| NGINX | 7589 | 6500 | 32 | Low |
| LiteSpeed | 8233 | 7200 | 28 | Efficient |
I never read such tables in isolation. If the RPS is correct but the CPU is at its limit, then threads or IO are limiting the Scaling. If RPS falls and latencies rise at the same time, I first resort to architectural changes. Small code fixes often only partially resolve congestion at global locks. A clean cut in thread and process models brings the Stability, that require productive systems [6].
Common causes in web environments
Global Locks Sessions or caches often cause the biggest bottlenecks. A single hotspot lock is enough to park many requests. High thread counts per core exacerbate the problem because the scheduler becomes overloaded. Synchronized IO calls in loops cause additional blocking and slow down workers in the wrong place. Added to this are database and cache collisions, which Latency Enlarge each request [2][3][5].
Server architecture also plays a role. Apache with prefork or worker naturally blocks more, while event-driven models such as NGINX or LiteSpeed avoid waiting points [6]. In PHP-FPM pools, pm.max_children causes unnecessary lock pressure when set too high. In WordPress, every uncached query leads to more competition on the DB and cache. This is exactly where I start before I add hardware for more IOPS or cores [2][6][8].
When contention can even be useful
Not every increase Contentionrate is poor. In scaling IO models such as IO completion ports or TPL in .NET, contention sometimes increases in parallel with throughput [3]. I therefore first measure goal metrics: RPS, P95 latency, and concurrent users. If RPS falls as contention increases, I take immediate action. However, if RPS increases and the Latency, I accept higher contention values because the system works more efficiently [3].
This perspective protects against blind optimization. I don't track individual counters without context. Response time, throughput, and error rate set the pace for me. Then I look at threads via profiling and decide whether locks, pools, or IO are the bottleneck. This is how I avoid Micro-optimizations, who miss the mark.

Strategies against thread contention: Architecture
I reduce Locks First, architecturally. Event-driven web servers such as NGINX or LiteSpeed avoid blocking workers and distribute IO more efficiently. I shard caches by key prefixes so that a hotspot doesn't cripple everything. For PHP, I use aggressive OPcache strategies and keep DB connections short. With the thread pool, I pay attention to the number of cores and limit workers so that the scheduler does not tip over [5][6].
Specific configuration helps quickly. For Apache, NGINX, and LiteSpeed setups, I stick to tried-and-tested thread and process rules. I like to summarize details about pool sizes, events, and MPMs in a compact form; a guide to Setting thread pools correctly. I take the actual load into account, not desired values from benchmarks. As soon as latency drops and the RPS rising steadily, I'm on the right track.
Strategies against thread contention: code and configuration
At the code level, I avoid global Locks and replace them, where possible, with atomic operations or lock-free structures. I equalize hot paths so that little is serialized. Async/await or non-blocking IO eliminate waiting times from the critical path. For databases, I separate read and write paths and make deliberate use of query caching. This reduces pressure on cache and DB locks and improves Response time noticeable [3][7].
With PHP-FPM, I intervene specifically in process control. The parameters pm, pm.max_children, pm.process_idle_timeout, and pm.max_requests determine load distribution. A pm.max_children value that is too high creates more competition than necessary. A sensible starting point is PHP-FPM pm.max_children in relation to the core count and memory footprint. This means that the pool responsive and does not block the entire machine [5][8].

Monitoring and diagnosis
I start with Goal-Metrics: RPS, P95/P99 latency, error rate. Then I check contention/sec per core, % processor time, and queue lengths. From about >100 contention/sec per core, I set alarms if RPS does not increase and latencies do not decrease [3]. For visualization, I use metric collectors and dashboards that neatly correlate threads and queues. This overview provides a good introduction to queues. Understanding server queues.
On the application side, I use tracing along the transactions. This allows me to mark critical locks, SQL statements, or cache accesses. I can then see exactly where threads are blocking and for how long. During testing, I gradually increase the parallelism and observe when the Latency bends. From these points, I derive the next tuning round [1][3].
Practical example: WordPress under load
Created with WordPress Hotspots plugins that send a lot of DB queries or block global options. I activate OPcache, use object cache with Redis, and shard keys by prefix. Page cache for anonymous users immediately reduces the dynamic load. In PHP-FPM, I size the pool just above the core number instead of expanding it. This way, I keep the RPS stable and response times predictable [2][8].
Without sharding, many requests face the same key lock. Then even a traffic spike can cause a cascade of blockages. I shorten the lock duration with lean queries, indexes, and short transactions. I make sure to use short TTLs for hot keys to avoid stampeding. These steps reduce the Contention visible and release reserves for peaks.

Checklist for quick wins
I start with Measurement: Baseline for RPS, latency, error rate, followed by a reproducible load test. Then I reduce threads per core and set realistic pool sizes. Next, I remove global locks in hot paths or replace them with finer locks. I convert servers to event-driven models or activate appropriate modules. Finally, I secure the improvements with dashboard alerts and repeated Tests from [3][5][6].
If problems persist, I prefer architectural options. Scale horizontally, use load balancers, outsource static content, and use edge caching. Then I equalize databases with read replicas and clear write paths. Hardware helps when IO is scarce: NVMe SSDs and more cores alleviate IO and CPU bottlenecks. Only when these steps are not enough do I move on to microwave-Optimizations in the code [4][8][9].
Choosing the right lock types
Not everyone Lock behaves the same under load. An exclusive mutex is simple, but quickly becomes a bottleneck for read-heavy paths. Reader-writer locks They relieve the load during many reads, but can lead to writer starvation during high write frequencies or unfair prioritization. Spinlocks help in very short critical sections, but burn CPU time under high contention—I therefore prefer sleeping primitives with futex support as soon as critical sections take longer. In hotpaths, I rely on Lock striping and shard data (e.g., by hash prefixes) so that not all requests require the same lock [3].
An often overlooked factor is the allocator. Global heaps with central locks (e.g., in libraries) lead to waiting points, even though the application code is clean. Per-thread caches or modern allocator strategies reduce these collisions. In PHP stacks, I make sure that expensive objects are reused or preheated outside of request hotpaths. And I avoid double-checked locking traps: I either do initialization at startup or via a one-time, thread-safe path.
Operating system and hardware factors
Plays on the OS NUMA plays a role. If processes are spread across nodes, cross-node accesses increase, and with them L3 and memory contention. I prefer to bind workers locally to NUMA and keep memory accesses close to the node. On the network side, I distribute interrupts across cores (RSS, IRQ affinities) so that one core does not handle all packets and clog the accept paths. Kernel queues are also hotspots: a list backlog that is too small or a missing SO_REUSEPORT creates unnecessary accept contention, while overly aggressive settings cause the Scaling can brake again – I measure and adjust iteratively [5].
In VMs or containers, I observe CPU throttling and steal times. Hard CPU limits in cgroups create latency spikes that feel like contention. I plan pools close to the guaranteed available cores and avoid oversubscription. Hyperthreading helps with IO-heavy workloads, but masks real core scarcity. A clear allocation of worker and interrupt cores often stabilizes P95 latencies more than pure raw performance.
Log details: HTTP/2/3, TLS, and connections
Keep-Alive Reduces Accept load, but binds connection slots. I set reasonable limits and restrict idle times so that a few long-running processes do not block capacity. With HTTP/2, multiplexing improves the pipeline, but internally, streams share resources—global locks in upstream clients (e.g., FastCGI, proxy pools) otherwise become bottlenecks. Packet loss causes TCP head-of-line, which slows down the Latency Increased significantly; I compensate with robust retries and short timeouts on upstream routes.
At TLS I pay attention to session resumption and efficient key rotation. Centralized ticket key stores require careful synchronization, otherwise a lock hotspot will occur in the handshake phase. I keep certificate chains lean and stack OCSP cleanly cached. These details reduce handshake load and prevent the crypto layer from indirectly throttling the web server thread pool.
Backpressure, load shedding, and timeouts
No system may accept unlimited amounts. I set Concurrency limits per upstream, limit queue lengths, and return 503 early if budgets are exhausted. This protects latency SLAs and prevents queues from building up uncontrollably. Backpressure I'll start at the edge: small accept backlogs, clear queue limits in app servers, short, consistent timeouts, and deadline propagation across all hops. This keeps resources free, and web hosting performance does not deteriorate in a cascade-like manner [3][6].
I use the following against cache stampedes Request coalescing One: identical, expensive misses run as a calculated request, while all others wait briefly for the result. For data paths with lock hotspots, the following helps single flight or deduplication in the worker. Circuit breakers for slow upstreams and adaptive concurrency (increase/decrease with P95 feedback) stabilize throughput and latency without setting hard upper limits everywhere.
Test strategy: load profile, regression protection, tail latency
I test with realistic Arrival rates, not just with fixed concurrency. Step and spike tests show when the system breaks down; soak tests reveal leaks and slow degradation. To avoid coordinated omission, I measure with a constant arrival rate and record actual waiting times. P95/P99 over time windows are important, not just mean values. A clean pre/post comparison after changes prevents supposed improvements from being mere measurement artifacts [1][6].
In the CI/CD pipeline, I set Performance gates: small, representative workloads before rollout, canary deployments with close monitoring of target metrics, and rapid rollbacks in case of deterioration. I define SLOs and an error budget; I stop measures that use up the budget early on, even if pure contention counters appear unremarkable.
Tools for in-depth analysis
For Linux, I use perfect (on-CPU, perf sched, perfect lock), pidstat and eBPF profiles to visualize off-CPU time and lock wait reasons. Flamegraphs on CPU and off-CPU show where threads are blocking. In PHP, the FPM slowlog and pool status help me; in databases, I look at lock and wait tables. At the web server level, I correlate $request_time with upstream times and see if bottlenecks are upstream or downstream of the web server [3][5].
I log trace IDs across all services and combine spans into transactions. This allows me to identify whether a global cache lock, a clogged connection pool queue, or an overflowing socket buffer is driving latency. This picture saves time because I can target the loudest bottleneck instead of flying blind with generic optimizations.
Anti-patterns that increase contention
- Too many threads per core: Creates scheduler and context switch pressure without doing more work.
- Global caches Without sharding: A key becomes a single point of contention.
- Synchronous logging In the hot path: File locks or I/O wait on every request.
- Long transactions in the DB: Locks are unnecessary and block downstream paths.
- Infinite queuesHide overload, shift the problem to the latency peak.
- „Optimizations“ without a basis for measurementLocal improvements often worsen global behavior [4][6].
Practice: Container and orchestration environments
When dumpster diving, I consider CPU and memory limits as hard limits. Throttling causes stuttering in the scheduler and thus apparent contention. I fix pool sizes to the guaranteed resources, set open file descriptors and sockets generously, and distribute ports and bindings so that reuse mechanisms (e.g., SO_REUSEPORT) to reduce the load on the accept paths. In Kubernetes, I avoid overcommitment for nodes that carry latency SLAs and pin critical pods to NUMA-friendly nodes.
I ensure that probes (readiness/liveness) do not trigger load spikes and that rolling updates do not temporarily overload the pools. Telemetry gets its own resources so that metric and log paths do not compete with payload. This keeps the web hosting performance Stable, even when the cluster is rotating or scaling.

Briefly summarized
Thread contention occurs when threads compete for shared resources and slow each other down in the process. This affects RPS, latency, and CPU efficiency and hits web servers with dynamic content particularly hard. I always evaluate contention in the context of target metrics so that I can identify real bottlenecks and solve them in a targeted manner. Architecture adjustments, reasonable pool sizes, lock-arm data paths, and event-driven servers deliver the greatest effects. With consistent monitoring, clear tests, and pragmatic changes, I achieve the web hosting performance back and keep reserves for traffic peaks [2][3][6][8].



